do you know anything about PhantomLance Backdoor? A group of hackers has been using Google Play to distribute malware that has been used to steal private data since late 2016.
Kaspersky Laboratories has shared a detailed report on the PhantomLance Trojan backdoor, dubbed a sophisticated form of malware, which is not only harder to detect but also harder to investigate.
Google Play Store apps infected by PhantomLance Backdoor have been stealing data since 2016
Kaspersky reports that the malware can basically gain access to all information on an infected smartphone:
The main goal of PhantomLance is to collect sensitive information from the victim's device. The malware can provide its collectors with location data, call logs, text messages, lists of installed apps, and complete information about the infected mobile phone.
Furthermore, its functionality can be extended at any time by simply uploading additional modules from the C&C server.
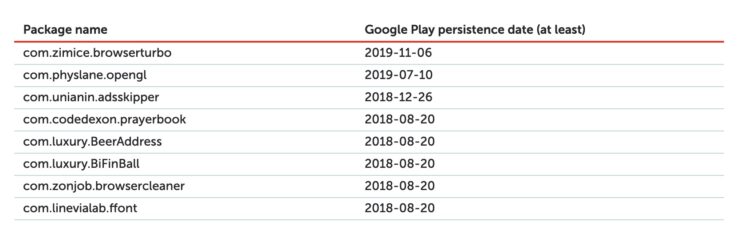
Malware in Google Play apps
During the investigation, the malware was found in popular apps and utilities that allow users to change fonts, remove ads, and perform system cleanups. The developers behind these apps were able to bypass any security checks on the Google Play Store by starting with non-malicious versions of their apps.
Once the apps were published, they were able to add malicious features later through updates, which the Google Play Store did not control. Developers were also able to create unique profiles on GitHub to act as credible development sources.
The main targets of PhantomLance have reportedly been users in Vietnam. However, infected apps have also been downloaded in other parts of the world. The Trojan has been linked to a group called OceanLotus, which has a history of similar malware attacks on desktop operating systems. These groups are often backed by high-level officials and even governments.
Although Google has removed these apps from the Play Store, they are still available online on various APK download websites and other third-party stores.
It seems that even if you only install apps from the Google Play Store, it is still not safe unless you verify the authenticity of the developers. A quick Google search can reveal a lot of credible information about the developers, and if something looks dubious in the search results, avoid such apps.
The open nature of Android can also work against it, as anyone can simply sign up for the Play Store and publish a malicious app.
This is still alarming for the world's most popular operating system, be it desktop or mobile. Android is used on 2.500 billion devices worldwide, and Google has repeatedly failed to provide adequate privacy and security guarantees to users for apps that are distributed through its official marketplace.
If you are interested in the technical background of how the malware works and the research that was carried out behind the scenes by Kaspersky Labs, read their detailed report here.